Why developing a cybersecurity safe culture is urgent?
How is it possible that after years of investing in cybersecurity defenses, still one phishing email can lead to a potential incident of a business at risk?
Technical software and procedures have been in place for years but still companies are facing issues with this initial point of access by hackers. Are companies unsuccessful in training their staff or are attackers getting more sophisticated?
It could be the first answer, as one of the trends in cybersecurity for 2022 is according to Gartner, a shift from traditional security awareness training towards an approach that is beyond compliance-based awareness campaigns and focused in holistic behaviour and culture change programs[1]. That implies that the current efforts on training employees on recognizing cybersecurity threats are not enough. Especially when looked at the key numbers of the human factor, one can imagine that this factor needs more attention.
The Human Factor in cybersecurity
Improving employee awareness and defense is critical to improve cybersecurity resilience
What are human risks within cybersecurity?
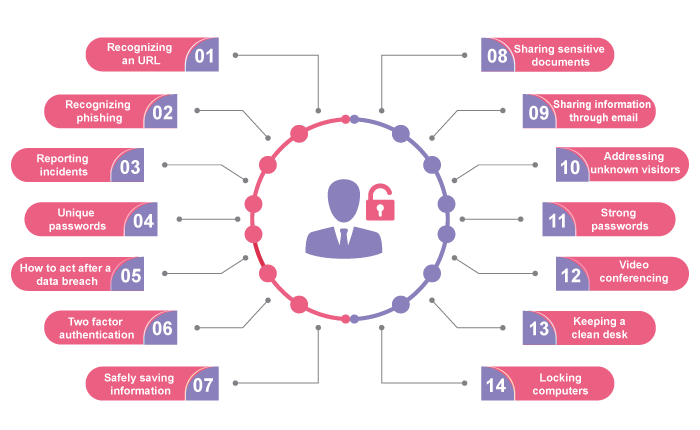
Bureau Veritas has looked at the 15 human risk topics related to human behaviour (Wetzer, 2022) :
For each of these, there is only so much you can do on the technical side. The real make-it-or-break-it factor of these 15 points is how the individual decides to behave. This raises the question of what drives individuals to behave safe or unsafe.
THE IMPORTANCE OF HUMAN RISK FACTORS IN CYBERSECURITY
As we have seen before, humans are often the weakest link in the chain of cybersecurity (Rhodes, 2001) and adopting the newest and best security technologies and solutions to protect your systems, still isn’t adequate without the help of your employees.
By understanding employees' reasoning, organizations can more effectively implement security technologies and policies (Sommestad, Karlzén, & Hallberg, 2015). With support from psychological models, organizations can focus on measuring & intervening with hands-on solutions that work for their employees.
What drives human behaviour?
Often, people know what they should do, but end up doing something different. We know that we shouldn’t text while driving, cross while the light is red or eat too much candy, but we still do it. In our daily life, there are thousands of examples just like these. It shows that only being aware of the correct behaviour doesn’t mean that you will actually do it. Most people know that they should have strong passwords, however, the average password strength is very weak in most organizations.
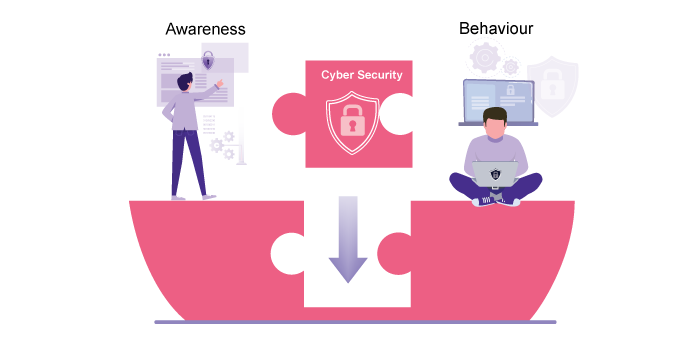
Therefore, we define a clear gap between awareness and behaviour and this is also the case within the realm of cybersecurity.
The message here is that only focusing your efforts on awareness won’t change the behaviour of anyone. On the contrary, what will change behaviour is focusing on lifting barriers and making sure that the end goal of policies and interventions is behaviour.
FOCUSSING ONLY ON AWARENESS WILL NOT CHANGE PEOPLE BEHAVIOUR
Psychologists have long known that behaviour can be explained in a multitude of ways. One of these ways is the MOA-model which explains that a certain behaviour only happens when a threshold of ability, motivation and opportunity is reached (O¨ lander & Thøgersen, 1995).
Finding out what are the barriers for behaving safely is central for a good cybersecurity approach within organizations. Only by researching these barriers can you create focused interventions that actually change behaviour.
ANTICIPATE HUMAN RISKS IN CYBER WITH OUR SAFE PROGRAM
For more effective protection against human error, Secura combined the expertise of security specialists with the expertise of psychologists to develop the SAFE Program.
This program is aimed at fulfilling the gap between awareness and behaviour based on the MOA model and supporting effective behavioural changes to make people acting safely and subsequently reduce cyber risks.
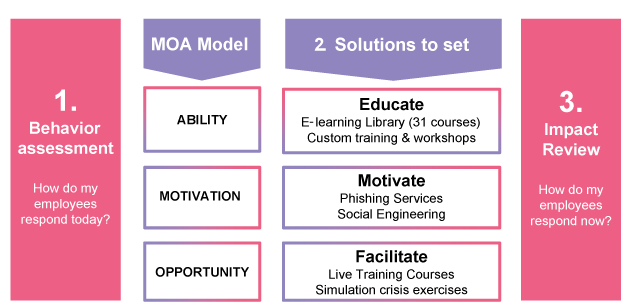
How does it work ?
- Based on a behaviour assessment of your employees, our team will support you in defining the best program content by combining different actions and timelines.
- With a combination of solutions like training courses, facilitation, workshops, social engineering services and crisis simulation, the SAFE Program will help people to act in the right way using the 3 levers of the MOA-model: ability, motivation and opportunity.
- Finally, an impact review with measure the behaviour change.
WHY DOES THE SAFE PROGRAM WORK?
With the SAFE approach, companies invest in creating awareness and achieving behavioral change that is tailored to the needs of the employees in your organization. As a result, the maturity level of information security increases, making the organization more resilient against outside attacks.
By choosing the SAFE program, it is also measurably clear, both internally and externally, that privacy and information security are of great importance to you.
SAFE demonstrably makes your employees more aware and competent to behave appropriately in case there are attempts by malicious parties to gain access to systems and information. With SAFE, your employees reduce the chance of incidents with a major impact and thus the associated high costs and the risk of reputation damage. In short: Better SAFE than sorry!
REFERENCES
[1] https://www.gartner.com/en/articles/7-top-trends-in-cybersecurity-for-2022
- Moore, S. (2022, April 13). 7 Top Trends in Cybersecurity for 2022. Retrieved from www.gartner.com: https://www.gartner.com/en/articles/7-top-trends-in-cybersecurity-for-2022
- O¨ lander, F., & Thøgersen, J. (1995). Understanding of consumer behaviour as a prerequisite for. Journal of Consumer Policy, 18(4), 345-385.
- Rhodes, K. (2001). Operations Security Awereness: The Mind has No Firewall. Computer Security Journal, 18:3.
- Sommestad, T., Karlzén, H., & Hallberg, J. (2015). A Meta-Analysis of Studies. International Journal of Information Security and Privacy, 9(1), 26-46.
- Wetzer, I. (2022). Onderzoek naar de human factor in informatiebeveiliging. Amsterdam: Secura.